Overview of ISMS
1. What is an ISMS?
IT systems and networks have become an indispensable social infrastructure today. On the other hand, there are a diversity of serious issues on information security: software such as malicious software seriously damage information systems, information leaks from the persons concerned, etc. The development and operation of an organization's ISMS through appropriate risk assessment against these threats is indispensable to ensure its overall inforamtion security.
An ISMS enables an organization to systematically operate its management system for information security. By establishing the ISMS, an organization can determine the necessary security level, create plans, distribute its assets, and operate systems based on its own risk assessment, along with individual technical countermeasures against each issue.
The key concept of the ISMS is to "preserve the confidentiality, integrity and availability of information by applying a risk management process and to give confidence to interested parties that risks are adequately managed". To do this, it is important that the ISMS is to be a part of, and integrated with, the organization's processes and overall management structure.
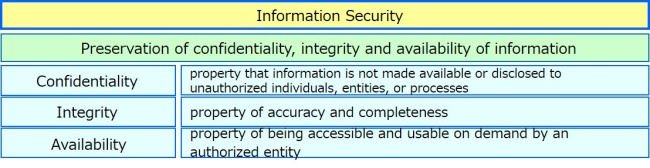
2. Three Elements of Information Security
In ISMS, the three major elements of information security are defined as the following:
NOTE: Other properties, such as authenticity, accountability, non-repudiation, and reliability can also be involved.
(ISO/IEC 27000)
3. What is ISO/IEC 27001?
Overview of ISO/IEC 27001
ISO/IEC 27001 is an international standard which specifies requirements for establishing, implementing, maintaining and continually improving an organization's ISMS.
It describes mainly what an organization should do for the establishment and implementation of an ISMS, rather than how to do it.
ISO/IEC 27001:2022 Information security, cybersecurity and privacy protection — Information security management systems — Requirements
(This standard has 1 amendment.
ISO/IEC 27001:2022/Amd 1:2024 Information security, cybersecurity and privacy protection — Information security management systems — Requirements
Amendment 1: Climate action changes)
This standard can be used:
● for managing changes in risks surrounding the organizational management and business processes;
In ISO/IEC 27001, it is specified that an organization shall establish and implement its ISMS, taking into consideration the organization's needs and objectives, information security requirements, processes used, as well as the size and structure of the organization.
This is helpful for an organization to reorganize its fundamental businesses to better manage changes in risks surrounding today's organizational management and business processes.
● as criteria to assess the organization's ability to meet its own information security requirements:
ISO/IEC 27001 can be used by internal parties as criteria to assess the organization's ability to meet its own information security requirements through performance evaluation and internal audits. It can also be used by external parties as criteria to assess the ability, which are called as second party audits or third party audits.
Structure of ISO/IEC 27001
ISO/IEC 27001 (JIS Q 27001) is a management system standard which applies common elements for ISO management systems standards (MSS) as a basis and specifies ISMS specific requirements indispensable to information security.
The structure of ISO/IEC 27001 is, therefore, consistent with that of other ISO Management System Standards as follows.
